To collect email authentication data and identify sources of DMARC failures, you need to configure three essential DNS records for your domain:
DMARC – the core policy and reporting mechanism
SPF – defines which IPs are allowed to send email on behalf of your domain
DKIM – verifies that messages haven’t been altered in transit
DMARC/eye helps you set these up step by step.
This is the most important record and the only one required for DMARC/eye to start collecting data.
Type: TXT
Name / Host: _dmarc
Value: (provided in the DMARC/eye setup panel)
Example:
v=DMARC1; p=none; rua=mailto:nwyg5cle@rua.dmarceye.com; fo=1; ri=86400;This record defines which IPs or services (e.g. Google, Mailchimp, Outlook) are allowed to send emails using your domain.
Type: TXT
Name / Host: @
Value example:
v=spf1 include:_spf.google.com include:mailgun.org -allYou should add all services you use for sending email. If the SPF is missing or incorrect, emails may fail authentication checks.
DKIM ensures that your messages haven’t been modified during delivery. Each email provider (e.g. Gmail, Mailchimp) has their own DKIM selector.
Type: TXT
Name / Host: something like default._domainkey or s1._domainkey
Value: provided by your sending service (not by DMARC/eye)
If you use multiple sending services, you may need multiple DKIM records with different selectors.
After setting the records, go back to DMARC/eye → Domains → Validate records
If everything is correct, your domain status will turn green and data will begin flowing within 24–48 hours
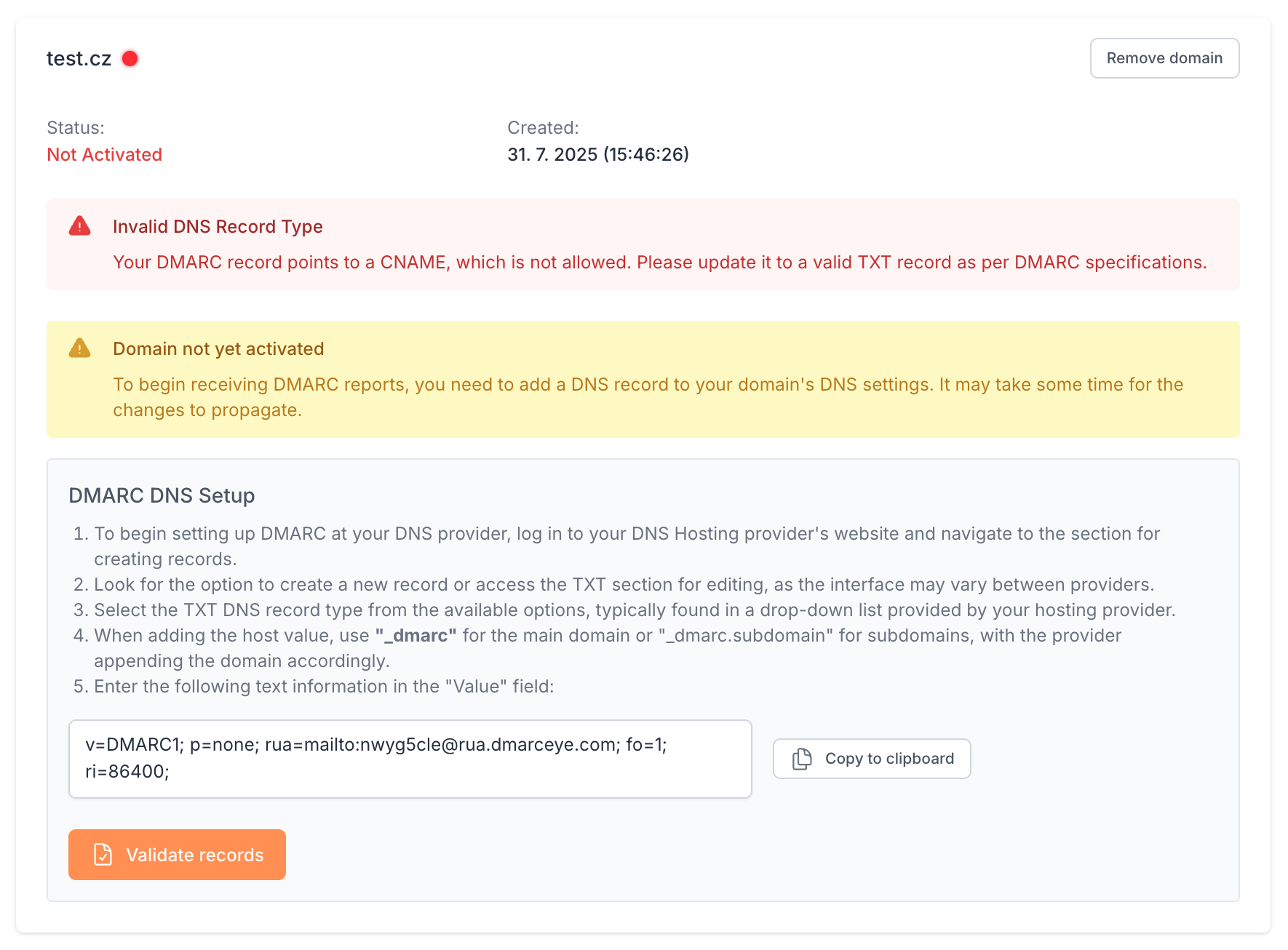
Wrong record type (e.g. CNAME instead of TXT)
Missing _dmarc in the host name
Extra spaces or broken line breaks in the value field
DNS changes not yet propagated